Although I work for CloudFlare there are some products that I haven't experienced as a customer and it's always fun and useful to actually behave as a customer and try them out. I like to do this to make sure the experience is good and try to spot bugs.
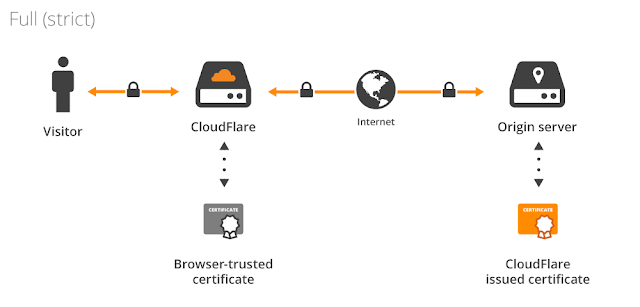
CloudFlare recently released a feature called Origin CA that generates a certificate you can drop onto your web server to ensure that the connection between CloudFlare and the server is secure. CloudFlare also offers a feature called Universal SSL that offers free SSL connections for the connection between a web browser and CloudFlare. Put the two together and you've got SSL from browser to CloudFlare and CloudFlare to the origin web server. Neat.
One of my domains, plan28.org, had a web site that was served over HTTP and I decided to SSL it using CloudFlare. I'd seen it demoed but there's nothing like trying it out for yourself. It was really quick to get set up. plan28.org is on CloudFlare's free tier.
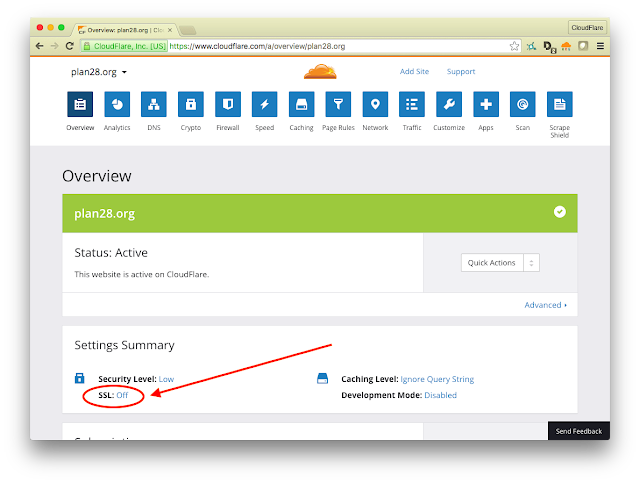
Here are the steps I took starting from logging into my account and verifying that I didn't have any SSL set up for this web site:
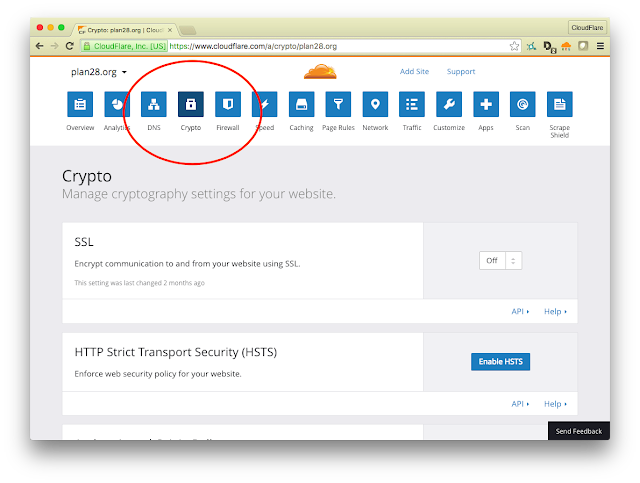
Then I clicked the Crypto button to get to the settings for Universal SSL and Origin CA.
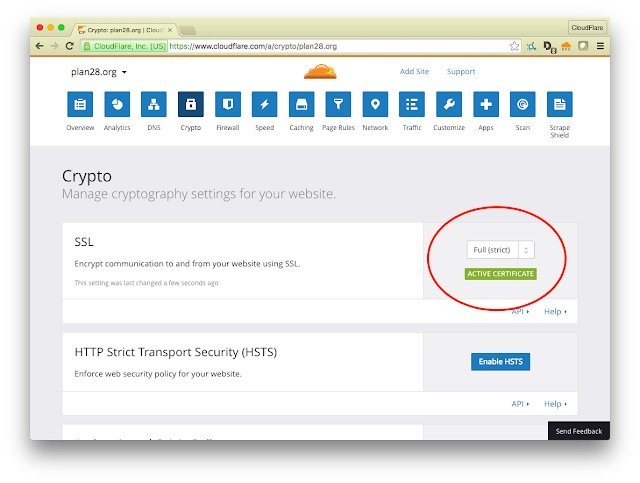
And I enabled SSL for the site by clicking the SSL button from Off to Full (Strict). That makes CloudFlare issue a certificate for plan28.org and start serving it publicly and at the same time ensure that it will secure the connection from CloudFlare to my web server by using SSL and checking the validity of the certificate that my web server presents.
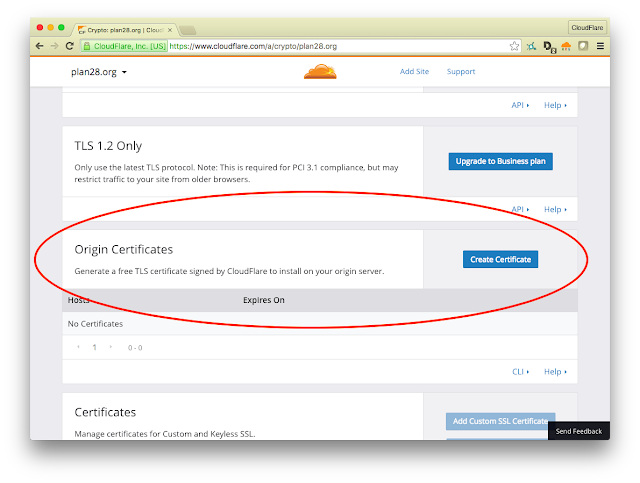
Boom. plan28.org was now available over http:// and https:// (although the latter wouldn't work until I had a valid certificate on the server). Next stop was a quick scroll down to find the Origin Certificates settings on the same page.
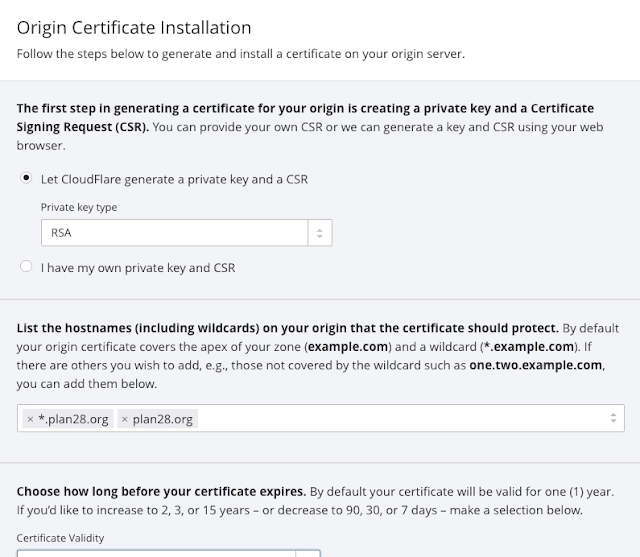
Clicking Create Certificate gave me a pop up where I could select the certificate type (RSA or ECDSA), validity period and add SAN names as needed.
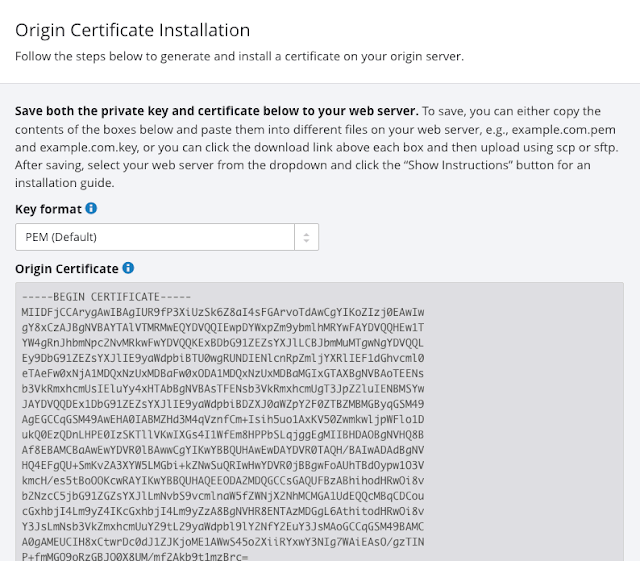
With those selected hitting Create resulted in the very fast creation of a certificate and the corresponding private key.
CloudFlare recently released a feature called Origin CA that generates a certificate you can drop onto your web server to ensure that the connection between CloudFlare and the server is secure. CloudFlare also offers a feature called Universal SSL that offers free SSL connections for the connection between a web browser and CloudFlare. Put the two together and you've got SSL from browser to CloudFlare and CloudFlare to the origin web server. Neat.
One of my domains, plan28.org, had a web site that was served over HTTP and I decided to SSL it using CloudFlare. I'd seen it demoed but there's nothing like trying it out for yourself. It was really quick to get set up. plan28.org is on CloudFlare's free tier.
Here are the steps I took starting from logging into my account and verifying that I didn't have any SSL set up for this web site:
Boom. plan28.org was now available over http:// and https:// (although the latter wouldn't work until I had a valid certificate on the server). Next stop was a quick scroll down to find the Origin Certificates settings on the same page.
Clicking Create Certificate gave me a pop up where I could select the certificate type (RSA or ECDSA), validity period and add SAN names as needed.
With those selected hitting Create resulted in the very fast creation of a certificate and the corresponding private key.
I copy and pasted them over to the server, configured NGINX for SSL, restarted NGINX and... it worked!
Total time: 10 minutes (most of which was messing around getting NGINX configured correctly). Now you can visit plan28.org securely.